In my previous article, I reviewed DefectDojo in the context of vulnerability management and DevSecOps processes. As a result, I wrote an article to share my experience with you — Vulnerability Management with DefectDojo.
A few days after publishing the article, the creators of DefectDojo contacted me and offered a DefectDojo Pro trial for a test drive. I was amazed that the creators of this well-known solution were interested in my opinion. Without waiting too long, I accepted the offer, and once again, I would like to share a review with you.
In this article, I am reviewing the capabilities, pros, and cons of DefectDojo Pro, particularly in the context of my last publication. Moreover, I had the opportunity to ask a number of questions to the creators to conduct an audit-like assessment in terms of data security, given that DefectDojo Pro is a cloud-based solution.
To be fully transparent, I would like to note that this is not a paid promotional article and I’m not receiving any compensation for writing it. I aim to keep my reviews trustworthy, as technical as possible, and valuable for DevSecOps practitioners and security professionals.
Differences Between Pro and OWASP Edition
DefectDojo Pro introduces several improvements when compared to the OWASP Edition. In my opinion, there are three main advantages that could convince engineers to consider using the paid version.
Cloud-Hosted Platform
DefectDojo Pro provides a cloud-hosted platform with all its benefits, including automatic updates. This is particularly advantageous for those who may find deploying the OWASP Edition and manually managing upgrades cumbersome. A cloud-based hosted solution has the potential to speed up the integration of vulnerability management into an organization, saving engineers time on configurations and management.
SAML/OAuth Authentication and MFA Support
DefectDojo Pro provides administrators the capability to set up SAML/OAuth authentication alongside Multi-Factor Authentication (MFA) via the web UI. Whereas in DefectDojo OWASP Edition, SAML and OAuth could be configured during deployment, the commercial version simplifies this process, allowing for easy enablement of these features.
Enhanced UI/UX with Dark Mode
DefectDojo Pro offers an improved user interface and experience, including a dark mode. This enhancement can contribute to a more user-friendly and visually comfortable environment for users.
It’s essential to consider that while cloud hosting may be a convenient solution for some engineers, certain companies may adhere to a strict approach regarding storing highly sensitive data in third-party ecosystems. However, the “Enterprise” edition also allows for self-hosting, providing companies with the option to maintain an improved version of DefectDojo while enjoying its benefits.
DefectDojo Pro has a number of other advantages such as:
- customizable dashboards
- enhanced notifications
- premium support with SLA
- tunable deduplication
- smart upload mechanism
The following screenshot presents how Defect Dojo Pro looks like after switching to the new UI:
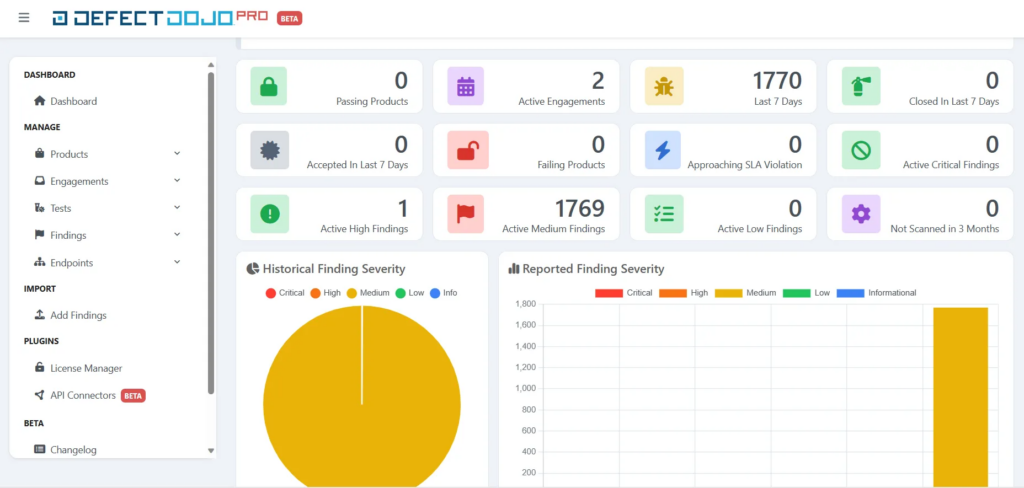
Security Review of DefectDojo Pro Cloud
During my review, I asked a number of audit-like questions to creators, and none of them were left unanswered. These questions align with the typical due diligence process which I had a chance to perform a number of times to choose the best suitable security solution for various use cases. Remembering that a cloud is just a someone else’s server we should make sure that data are properly processed. This time, I was focused mainly on data security and tenants separation mechanisms as DefectDojo Pro stores data in the cloud.

Data Security
In terms of data security, all of data are encrypted both at rest and in-transit, including backups. Data of each customer are encrypted with a dedicated encryption key. Furthermore, customers are able to supply their own encryption keys and other relevant parameters.
To separate customers and achieve an increased level of security, each of them have a dedicated database in a virtually separated environment. Each environment have a dedicated resources for performance. For additional security measures, Endpoint Detection and Response (EDR) was implemented in the hosted environment with proper audit logging. For more demanding customers, there is also DefectDojo Enterprise edition which allows for self-hosting the application in a customer’s environment. Based on the provided answers, the Enterprise edition have the same capabilities as cloud instance.
Authentication and Authorisation Mechanisms
DefectDojo Pro introduces several authentication improvements compared to the OWASP Edition. Firstly, it enables the configuration of Security Assertion Markup Language (SAML) and OAuth in web UI, catering to the needs of more demanding organizations. With such feature, it’s possible to implement a centralised Identity and Access Management with a single provider for all users across various systems. Regarding OAuth, the following screenshot illustrates providers that can be configured:
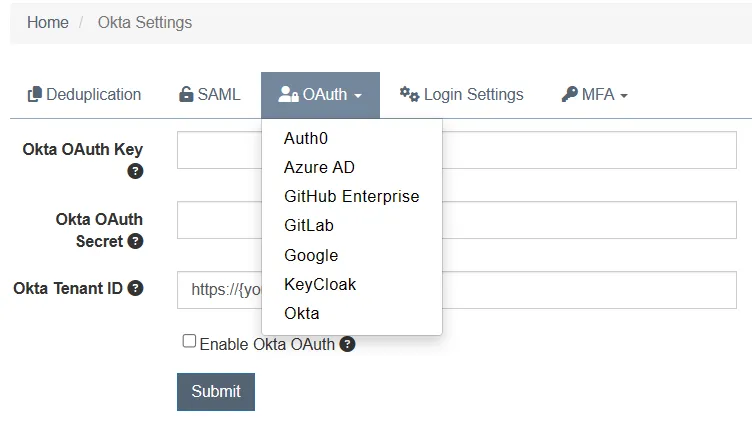
It should be noted that OAuth, SAML and LDAP can be also configured in DefectDojo OWASP Edition but it requires more configurations efforts. More details about authentication mechanisms in a free version can be found in the Integrations section of DefectDojo documentation.
Another improvement is a settings page that allows customization of login mechanisms, as presented below:
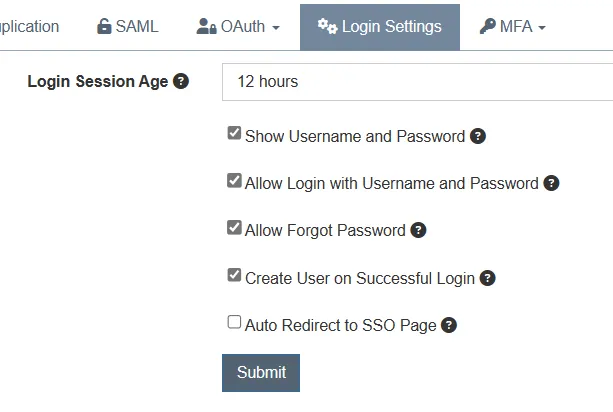
With this settings view, we can fully disable username and password login in favour of OAuth or SAML. Furthermore, if we prefer username and password, it’s possible to disable the “Forgot Password” feature which might be abused by potential attackers.
Another advantage is Multi-Factor Authentication (MFA), which can be enabled and required globally for all users. MFA can be configured by scanning QR codes in apps such as Google Authenticator.
Last but not least, the portal allows to configure network firewall rules using subnet masks to make sure that only machines with trusted IP addresses can connecto to the portal. I described this configuration in Onboarding Experience section of this article.
Customer’s Support
All cloud instances come with customer support, which encompasses bug fixes, assistance with best practices, and remote troubleshooting. The standard Service Level Agreement (SLA) for Basic Support ensures a response within 3 business days, which is guaranteed. With Rapid Support, this is reduced to 1 business day. However, the creators have assured that they typically respond to customers much faster than the SLA agreements.
Secure Development
Last but not least, the creators of DefectDojo Pro ensure that their solution maintains the highest security standards by conducting both third-party and internal penetration testing regularly. Since DefectDojo OWASP Edition is an open-source solution, it benefits from scrutiny by numerous researchers, thereby enhancing code security coverage.
Here’s a fun fact about securing DefectDojo: developers use another DefectDojo Pro instance to keep an eye on security scans performed against DefectDojo during development. It’s like having a digital watchdog that’s actually keeping secure another version of itself!

Enhanced UI, UX and Dashboards
DefectDojo Pro offers an enhanced UI which looks really cool at first glance. The following screenshot presents a product view of my example Damn Vulnerable App.
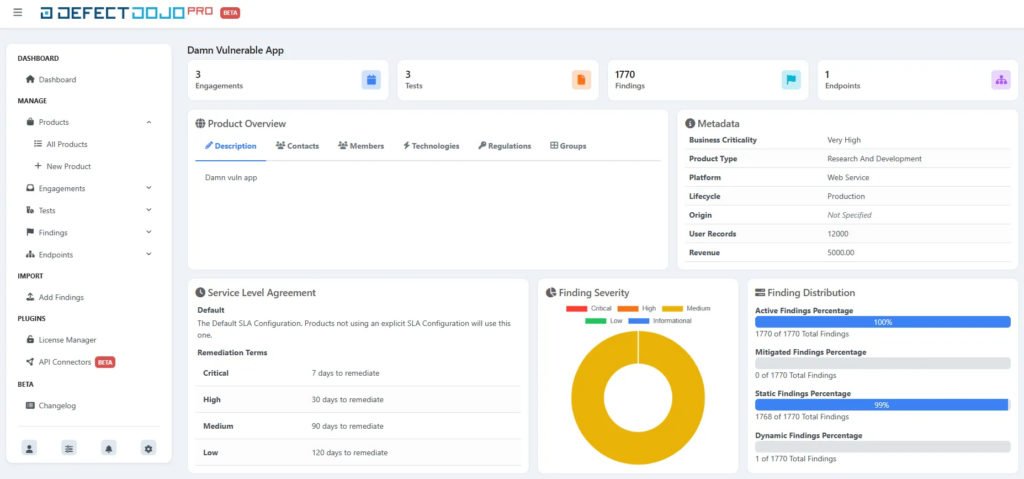
It should be noted that the new UI is still under development, and there are areas where improvements can be made. This feature is marked as a beta feature. In terms of data viewing, the beta UI offers a much better experience than the previous one, with a fresh and modern look. However, it may not be reliable for all use cases, particularly when it comes to inserting new data into the portal or modifying existing data. During my review, I noticed that some API calls were not handled properly, resulting in some odd behaviors. In all such cases, the old classic UI can still be used.
In general, I had a positive experience with viewing data in the new UI, which could be an advantage for product owners and engineers working on fixing vulnerabilities. For users who will modify data within the portal, it’s still possible to use the old UI.
Below, you can find a few screenshots from the new UI.
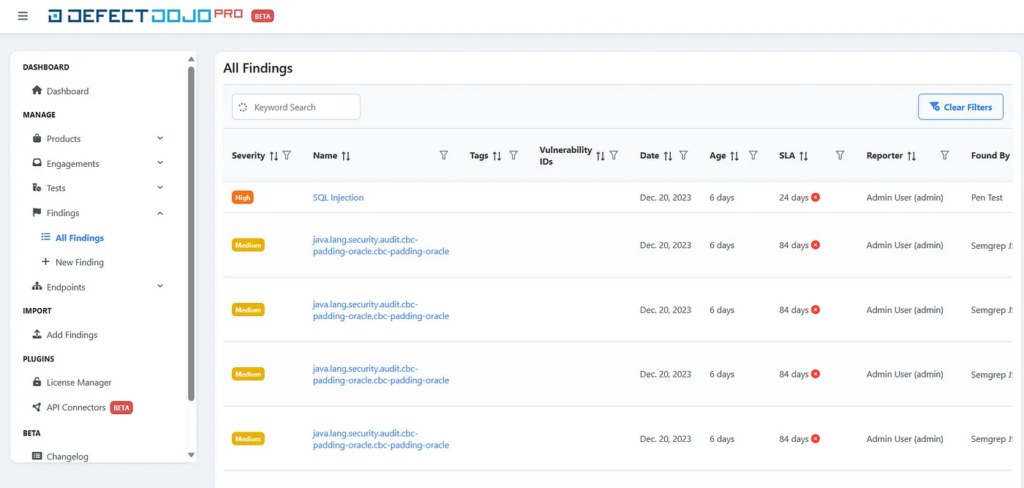
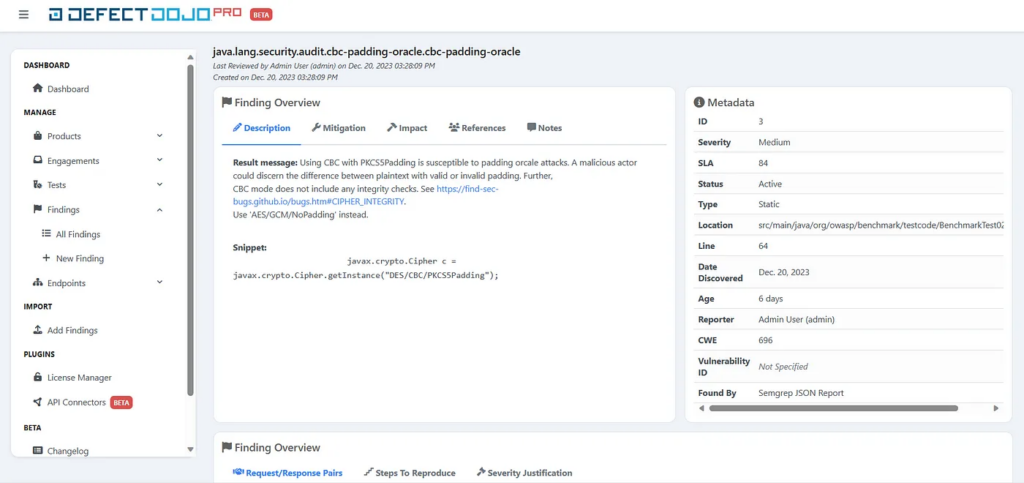
The following screenshot presents an example finding imported from a Semgrep report. This finding view is significantly improved compared to the old UI. When looking at this page, it’s easier to obtain the most important information about the security issue. It also contains a Metadata section with various pieces of data that were not visible in the old UI.
In terms of dashboards, at the time of writing this article, it was not possible to configure them within the new UI. However, it was possible to adjust dashboards when switched to the old one. The configuration allowed me to edit basic display settings to show and hide some sections, as presented below:
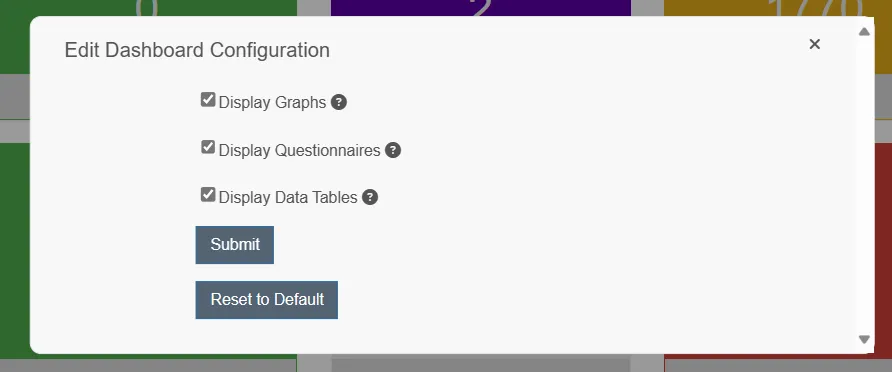
Furthermore, it was possible to add new tiles to the main dashboard. It should be noted that all of the changes were reflected in the beta UI.
Onboarding Experience
The onboarding process for DefectDojo Pro was a straightforward one. It allowed the specification of the domain for the cloud instance, the region where data would be stored, and firewall rules. The following screenshot presents the process.
Firstly, we observe a “Welcome” message:
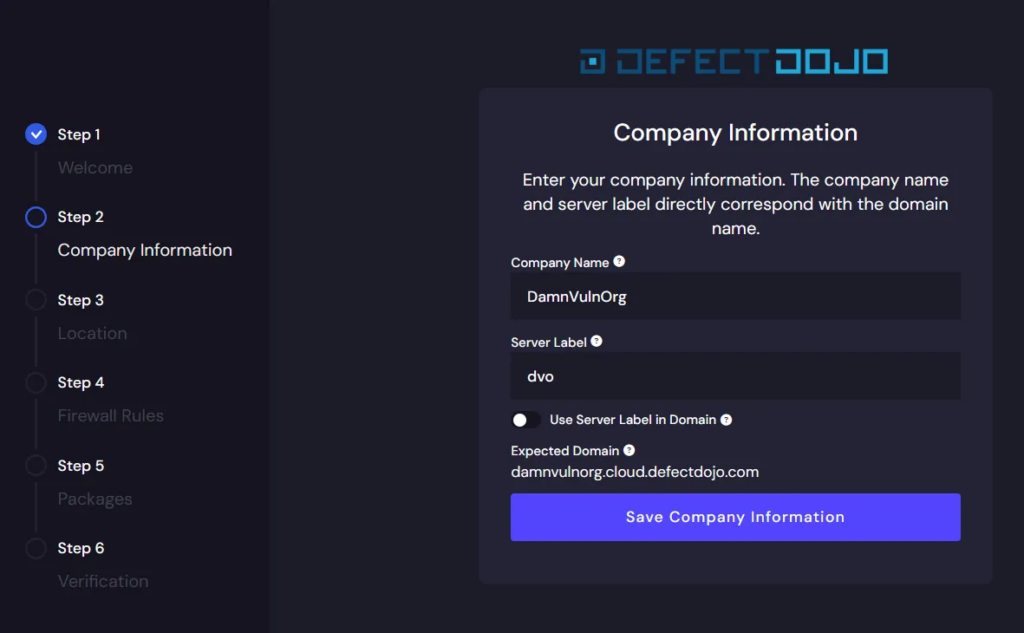
Next, we need to provide basic information about the company, which will be used as a subdomain. The expected domain is shown below after filling in the “Company Name” field. In my case, I chose “DamnVulnOrg”.
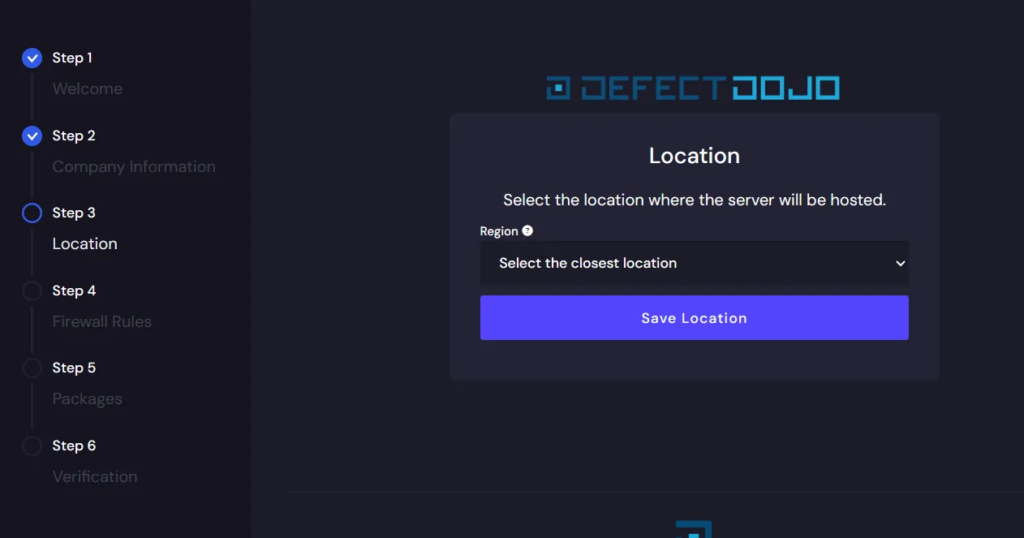
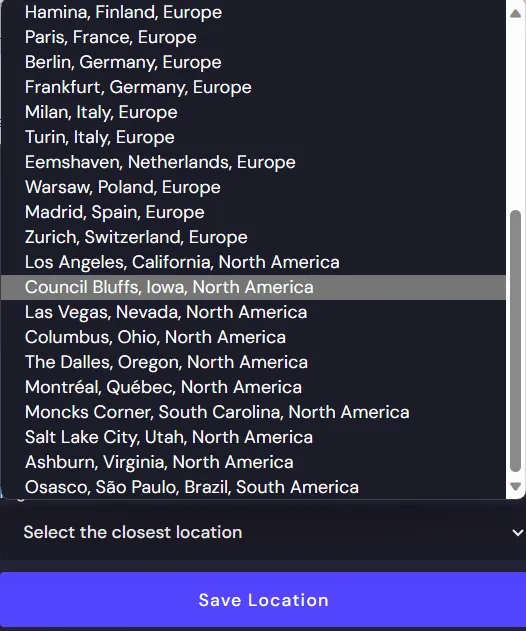
The next step was quite surprising for me, as it was possible to choose a region where data would be hosted. I was surprised not only by the option to select the location but also by the number of possible locations, which can be a significant advantage from a regulatory and compliance perspective.
The following screenshots presents how many locations can be chosen:
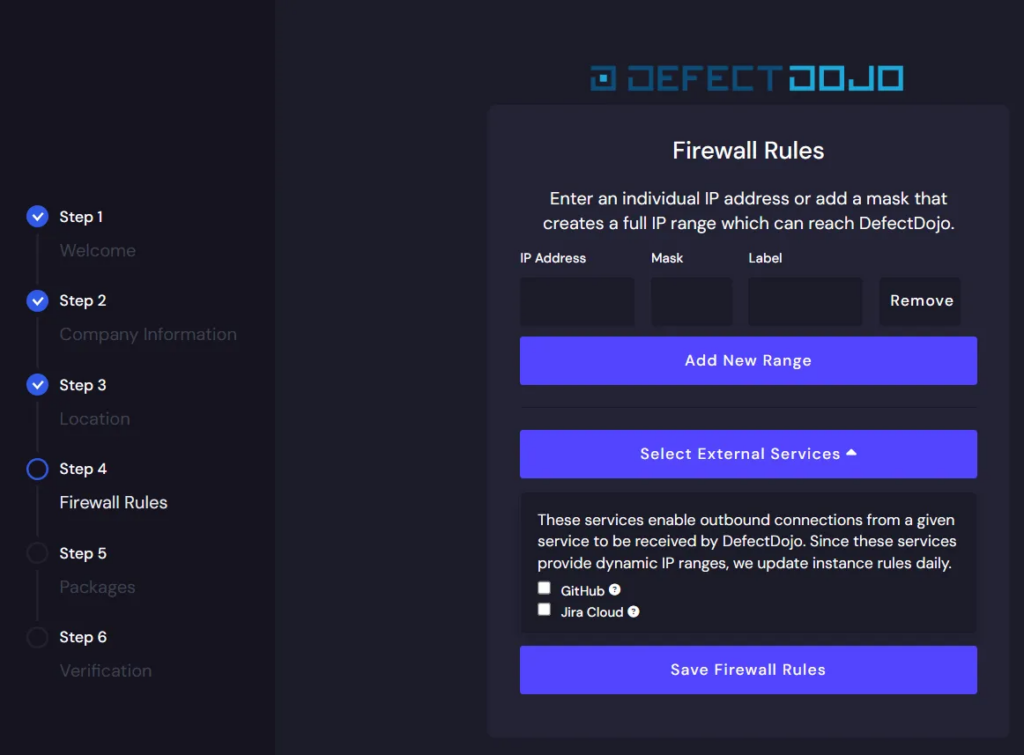
The next step allowed setting firewall rules that would be used for accessing the DefectDojo portal. Unfortunately, this is still a missing feature in a number of cloud-based solutions. With this configuration, it’s possible to limit access to the DefectDojo dashboard only for users with traffic originating from trusted networks, such as the company VPN, etc. Furthermore, as we can observe in the screenshot, GitHub and Jira Cloud IP addresses can be added automatically to firewall rules, so we don’t have to manage those rules manually.
The next steps were related to choosing a plan and verification. In my case, the verification process took 2 hours, and after that, the account was active and ready to use. In the final email, I received one-time-use credentials to log in to the portal. Upon the first login, I had to change the credentials. One of the first things I did was also switch to the new UI, which is still an optional feature. It can be achieved by clicking on the “New UI” button from the top right corner drop-down menu.
In general, the onboarding process was brief and straightforward, yet it allowed for configuring the most important aspects required from a cloud-based platform — location and firewall rules. Overall, the onboarding experience was quite positive from my perspective.
Summary
I have to be honest with you that I was reviewing this solution with a great curious and hope to see improvements in areas where OWASP Edition had some well known issues or was… let’s say challenging for engineers. I have to admit that my assumptions were pretty accurate which I’m happy about.
As a cybersecurity enthusiast who danced with various commercial solutions, some of them felt like they were designed by people who’ve only read about hacking in a book. But Defect Dojo Pro? Based on the offered features and security standards, it’s definitely designed by security professionals for security professionals.
For a medium and larger size companies, the pricing is competitive as it starts from 1250$ per month to store up to 20k vulnerabilities. As a medium size company, I understand a company with no more than 50k vulnerabilities — btw. it’s a really unique metric to measure company size by a number of vulnerabilities.
If you’re looking for a centralised vulnerability management solution that will gather, store and analyse thousands of vulnerabilities in one place, DefectDojo Pro is definitely one of the platforms worth to consider. If you have more demanding use cases and some aspects of cloud-based solution may not meet your regulatory requirements, you may want to take a look at self-hosted “Enterprise” edition.
Finally, let’s take a look at the Pros & Cons of DefectDojo Pro. It should be noted that all of the advantages of DefectDojo OWASP Edition are applicable to DefectDojo Pro. They can be found in my previous article.
Pros
- OAuth and SAML integrations
- MFA support
- customer’s support replying under SLA
- cloud-based solution with high security standards
- self-hosting still available for more demanding users with “Enterprise” license
- currently, the price is very competetive for such robust solution
Cons
- still, it’s under development, and some beta features may not be reliable in certain use cases
- for smaller organisations it might be too complex
Last but not least, I would like to thank DefectDojo Team for providing me a trial version of DefectDojo Pro for the review.