In this article, I’m presenting the Exploit Prediction Scoring System and its practical use cases in tandem with Common Vulnerability Scoring System.
Nowadays, the most popular scoring system used for security vulnerabilities is certainly the Common Vulnerability Scoring System (CVSS). CVSS is a valuable mechanism for identifying the principal characteristics of a vulnerability. Based on these characteristics, a CVSS score can be calculated to assign severity and priority for remedial actions. However, is it good enough to use only CVSS for prioritization? In my opinion, CVSS is sufficient for most organizations to understand the severity of a vulnerability. Still, when it comes to prioritization, I would recommend incorporating additional contextual data and other scoring mechanisms, such as the Exploit Prediction Scoring System (EPSS).
In this article, I’m covering what EPSS is, its purposes and how it can be utilised to calculate priorities for remedial actions in the context of vulnerability management.

What is EPSS?
EPSS is Exploit Prediction Scoring System which is greatly explain by the definition available on the official FIRST website:
The Exploit Prediction Scoring System (EPSS) is a data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild.
The EPSS model estimates the likelihood (probability) that a software will be exploited in the wild, producing a score ranging from 0 to 1 (or 0 to 100%). A higher score indicates a greater probability of a vulnerability being exploited. EPSS not only offers scoring based on vulnerability characteristics but also incorporates current threat data from Common Vulnerability and Exposures (CVE) database.
EPSS was introduced by the EPSS Special Interest Group, which is a part of FIRST — Forum of Incident Response and Security Teams. FIRST is the premier organization and recognized global leader in incident response, leading a number of initiatives, including the development of CVSS. It is possible to join the EPSS Special Interest Group by submitting a request through the FIRST website at first.org. The group have a regular weekly meetings and it’s also possible to receive updates through mailing list or Slack.
Compared to CVSS, EPSS includes an extra factor about exploitation likelihood. The exploitation likelihood is a very valuable factor as it allows to better understand the threat. By utilizing this score, we can enhance our ability to identify threats and prioritize security issues with a high exploitation likelihood. As an example, in this article, I will present a case where certain medium-severity issues may take precedence over high-severity issues due to their higher exploitation likelihood.
How to Calculate EPSS?
EPSS is calculated using a model maintained by its creators. Scoring for each CVE can be obtained from CSV file published regularly at official website. Alternatively, it can be calculated by utilising the official API. I will present both methods below.
If you’re looking for a user-friendly web application to calculate EPSS, you might be interested in my project – EPSS Calculator.
Calculating EPSS with CSV File
Scores are generated daily and they are published in EPSS Data and Statistics website as a CSV file which can be easily downloaded.

The following image displays the first few entries from the downloaded file with EPSS scores, allowing you to observe the initial CVEs dating back to 1999.
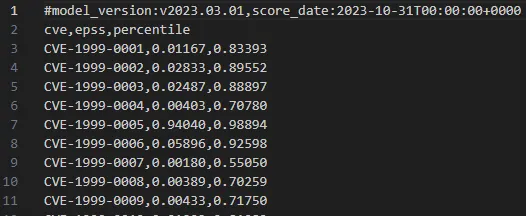
On the screenshot presented above, you can see that the file consists three columns separated by commas. The first column contains the CVE identifier, the second column contains the EPSS score (exploitation likelihood), and the last column contains the percentile, which represents the percentage of vulnerabilities with an equal or lower EPSS score.
The difference between the EPSS Score (EPSS Probability) and the percentile is illustrated on the diagram below.
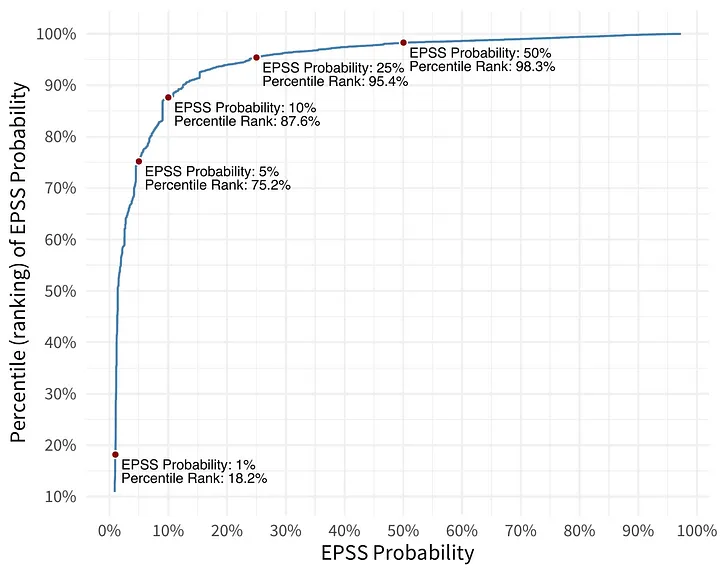
A higher exploitation probability will correspond to a higher percentile rank. Based on the diagram, we can deduce that vulnerabilities with an EPSS score equal to or less than 1% account for approximately 18.2% of all vulnerabilities. In other words, nearly 20% of all CVEs have a maximum exploitation likelihood of 1%.
Furthermore, based on this diagram, we can also conclude that only 1.7% of all CVEs have an exploitation likelihood greater than 50%. It’s indeed a cool scoring system! 😉
Probabilities and percentiles are deeply explained in How to understand and interpret EPSS Scores at official website which I can recommend if the above explanation is not enough for you.
As you may know, I really enjoy using Python for automating security activities and I would like to share with you a short code for obtaining EPSS score for a chosen CVE from a CSV file.
Firstly, let’s download and decompress CSV file:
wget https://epss.cyentia.com/epss_scores-current.csv.gz && gzip -d epss_scores-current.csv.gzThe following Python code returns EPSS for Log4j vulnerability — CVE-2021–44228 using the downloaded CSV as a source file for EPSS data.
import csv
epss_csv_location = "epss_scores-current.csv"
cve_to_calculate = "CVE-2021-44228" # Log4j
# creating empty dict to store data
# keys are CVE identifiers and values are EPSS scores
cves_to_epss = {}
with open(epss_csv_location, 'r') as data:
for line in csv.reader(data):
cve = line[0] # CVE is at first position
epss_score = line[1] # EPSS score is at second position
cves_to_epss[cve] = epss_score
score = cves_to_epss.get(cve_to_calculate)
print(f"EPSS Score of {cve_to_calculate} is {score}")The output from the script is presented below:
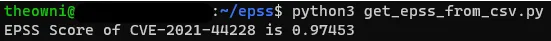
As you can see the likelihood of exploiting Log4j vulnerability is over 97%!
If you’re interested about more Python tricks and useful libraries, I recommend to take a look at dedicated article — Python for DevSecOps and Any Security Engineer.
Calculating EPSS with API
FIRST organisation provides an API for calculating EPSS, which can be used for various scenarios, such as:
- obtaining the current scoring for chosen CVEs,
- obtaining historical scoring for chosen CVEs from the past 30 days,
- obtaining CVEs with the highest scoring.
As EPSS scoring might change over the time for the same CVE, it might be useful to obtain also historical data in some cases. Scoring may change especially for newly released CVEs. At the release date, they may have a relatively low EPSS score that may increase over the time.
To obtain EPSS score for a specific CVE, the following API endpoint can be used:
The API output is presented below:
{
"status": "OK",
"status-code": 200,
"version": "1.0",
"access": "public",
"total": 1,
"offset": 0,
"limit": 100,
"data": [
{
"cve": "CVE-2021-44228",
"epss": "0.974530000",
"percentile": "0.999420000",
"date": "2023-11-01"
}
]
}As you can observe, the same EPSS score is returned as the one presented in CSV file — 0.974530000. I couldn’t handle myself and I quickly wrote very simple script for obtaining EPSS score from the API with Python:
import requests
cve_id = "CVE-2021-44228"
url = f"https://api.first.org/data/v1/epss?cve={cve_id}"
response = requests.get(url)
data = response.json()
epss_score = data.get("data")[0].get("epss")
print(f"EPSS Score of {cve_id} is {epss_score}")
I noticed that there are also a few open-source EPSS API clients available on GitHub which you can easily find. I don’t want to recommend any specific tool as they’re not official clients and they’re rather simple to implement. For more details about API, I recommend to take a look at EPSS API official documentation.
It’s important to note that, at the time of writing this article, there is no offline EPSS calculator available, and all scores are calculated for CVEs. However, there may be initiatives to implement an offline mechanism for calculating EPSS for vulnerabilities without CVEs, as EPSS is constantly evolving and improving.
If you have concerns about using the EPSS API as the communication or server logs may expose data about vulnerabilities that you’re affected, I would suggest downloading the CSV file with all of the calculation results as a more secure alternative.
Prioritising Remedial Actions with EPSS
EPSS is used by a number of companies and products for prioritising remedial actions. As authors says, “EPSS shouldn’t be treated as a complete picture of risk, but it can be used as one of the inputs into risk analyses” and “EPSS specifically helps measure threats”. I completely agree with these statements, and in my opinion, EPSS should be used in conjunction with other scoring mechanisms, such as CVSS, to prioritise remedial actions.
To achieve this, I can propose a basic mathematical formula for defining a priority score. This score can be employed to prioritize remedial actions for vulnerabilities with the highest score. The priority score can be calculated based on several factors, each with its own weight. You can use a weighted arithmetic mean formula to produce a priority score based on several factors:
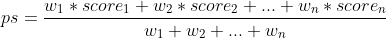
Now, let’s calculate priority score with proposed formula based on CVSS and EPSS factors. For this purpose, we will need to normalise the scores to have them in the same range and define the weights. For weigths, I will use 4 for EPSS and 6 for CVSS score. It means, that CVSS will be more important than EPSS for prioritisation but EPSS will be still relevant. I will also normalise the score to have both of them as a number between 0 and 100. In this way, priority score will be also a number between 0 and 100:
- as CVSS score is between 0 and 10, I will multiply it by 10,
- in terms of EPSS, I will multiple it by 100 as normally it’s a number between 0 and 1.
The final priority score formula that takes into account CVSS and EPSS is presented below. This formula also normalizes them to the range of 0 to 100.
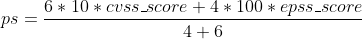
To present you with an example result, the priority score for Log4j vulnerability would be 98.9812.
Let’s consider another example — CVE-2023–38039, a Denial of Service vulnerability identified in cURL. It has a CVSS score of 7.5, but its EPSS score is only 0.000950000 — not likely to be exploited in the wild. In my opinion, the EPSS score seems reasonable because this vulnerability requires specific conditions to be exploited, and the impact may be much lower than presented. Additionally, a successfull exploit may require a significant efforts from attackers but may not provide substantial value. After using the suggested formula, the priority score would be 45.038. Lookig at this number, we can say that by adding EPSS factor, we strongly reduced priority score of this vulnerability. This reflects that it may not be as attractive to attackers as the CVSS score might suggest.
The above priority score formula is just a proposal which I’ve just created for the purposes of this article and for sure can be improved. Especially weights can be adjusted for your needs. Moreover, you can add more context factors to this formula. I’m more than happy to see comments about that prioritisation approach and get some ideas about your approach to this topic!
Summary
As you could observe, EPSS is a very innovative scoring system that goes beyond vulnerability characteristics by considering various data about CVEs. It’s important to note that this scoring mechanism is currently used exclusively for vulnerabilities with assigned CVEs. Additionally, EPSS is primarily about measuring the threat associated with a vulnerability, not its impact or severity.
EPSS is not designed to replace all other scoring mechanisms but should be seen as an additional factor to enhance the understanding of the threat and potentially a priority in the context of vulnerability management. It’s not enough to rely only on this factor for prioritisng remedial actions. Similarly, it’s not enough to use only CVSS for prioritisation remedial actions as it was presented in previous section with cURL vulnerability.
I hope you got enough information to understand EPSS and you enjoyed my dirty priority score formula. In my next articles, I’m going to cover more aspects of vulnerability management, focusing on technical aspects. Stay tuned! 🚀🚀🚀





