In this article, I’m presenting DefectDojo platform which is an open-source solution dedicated for vulnerability management but also offers a number of other security related features. As usual in my articles, I’m providing technical details about implementating DevSecOps stuff. Also, in this case I will present how to deploy DefectDojo with Docker. Furthermore, you will find here a little bit of theory about Vulnerability Management and some tips for you to implement this process in the most effective way.

Vulnerability Management with DefectDojo
What is Vulnerability Management?
Before presenting DefectDojo capabilities for tracking vulnerabilities, let’s clarify what we understand by a Vulnerability Management term. The below definition is the most suitable in my opinion:
Vulnerability Management is the ongoing, regular process of identifying, assessing, reporting on, managing and remediating security vulnerabilities across endpoints, workloads, and systems.
This definition greatly presents that Vulnerability Management as many other cyber security related processes is not a one-time task but is an ongoing process.
Vulerabilities can be identified in a number of different ways, starting from manual internal security assessments, through red team, pentests, bug bounty programs and finishing on automated solutions that can identify and report findings nearly in a real time. To track those findings effectively we need a platform that will allow to gather and track all of them through their lifecycle — from identifying the issue to remediating it. Such platform can be implemented in a various ways. Common approach is to use task management solution and treat each finding as a separate ticket. It’s also the most cost-effective and time-effective approach in terms of implementation and management. However, to implement the most effecive process with many integrations, solutions such as DefectDojo can be considered.
Introduction to DefectDojo
As we can read from DefectDojo GitHub repository page:
DefectDojo is a security orchestration and vulnerability management platform. DefectDojo allows you to manage your application security program, maintain product and application information, triage vulnerabilities and push findings to systems like JIRA and Slack.
Comparing the DefectDojo description with our Vulnerability Management definition, it looks really promising. In terms of technical aspects, DefectDojo is a web application that was developed with Python and Django. It uses SQL relational database where PostgreSQL or MySQL can be configured. It also uses Celery for some scheduled tasks such as automated findings deduplication and JIRA synchronisation. Furthermore, RabbitMQ (or Redis) is used as a messsage broker for asynchronous execution. Those components are presented on the architecture diagram below:
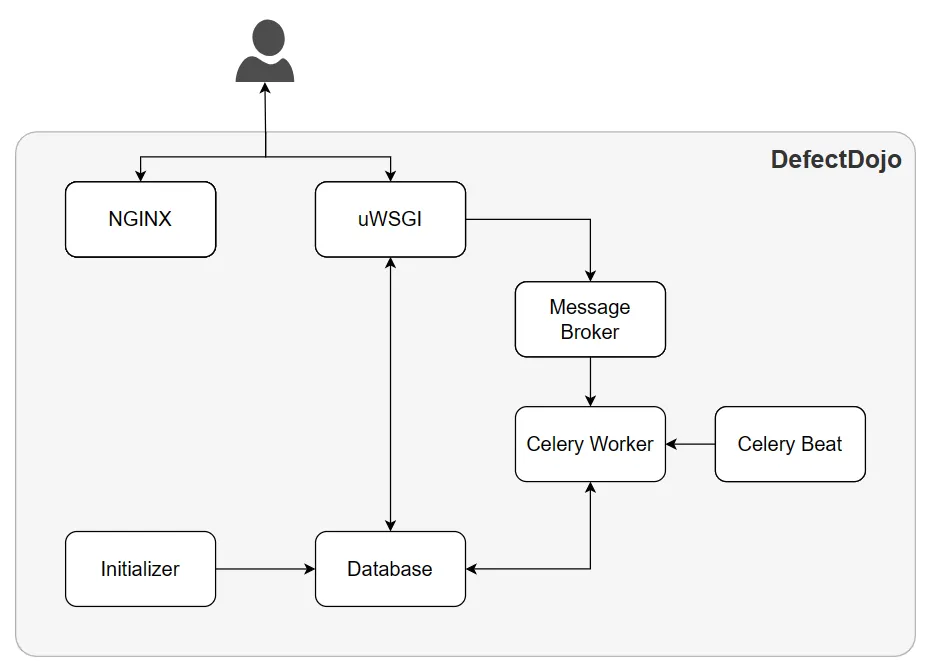
We know what DefectDojo is and how it’s built, let’s see an overview of what DefectDojo offers:
- tracking vulnerabilities and security engagements which is ready to use out of the box
- tracking products / components with various details
- custom metrics with dashboards
- benchmarks and questionnaires for tracked products
- API
Deploying DefectDojo
DefectDojo can be deployed with Docker Compose. For deployment it is suggested to have at least 2 vCPUs, 8GB of RAM and 2GB of disk space. However, the suggested 2GB of disk space doesn’t include database storage and this value should be considered before database deployment.
For the purposes of this article, I’m deploying DefectDojo locally with Docker Compose. It is required to install Docker and Docker Compose to replicate my instructions. Firstly, DefectDojo repository has to be cloned with the following command:
git clone https://github.com/DefectDojo/django-DefectDojo.gitNow, let’s change directory do django-DefectDojo, set environment variables and deploy DefectDojo in postgres-redis profile with the following commands:
# change directory to the cloned repository
cd django-DefectDojo
# set environmental variables required for running containers
./docker/setEnv.sh
# run containers with Docker Compose Up using preconfigured settings
./dc-up.sh postgres-redisDefectDojo offers a few profiles with different deployment approaches. The above script uses PostgreSQL and Redis as databases. But, if you prefer MySQL as relational database, it can be used too by specifying mysql-redis instead of posgres-redis. Also, redis can be replaced with rabbitmq.
After waiting a few moments, DefectDojo is deployed locally on http://localhost:8080/. Admin user is created by the initialisation script at the first deployment if adminuser does not exist. A password for this user is automatically generated and can be observed in logs filtering by Admin password: pattern. These credentials can be used to log in to web application for the first time.
After entering username and password you should observe DefectDojo dashboard:
In next sections, I’m describing specific aspects of working with DefectDojo on various examples.
Deploying DefectDojo in a Production
For production purposes, I suggest to use dc-up-d.sh script from a root project directory and adjust values in docker-compose.yml file. The content of this file should be reviewed carefully and modified, especially in terms of secrets. Furthermore, after the deployment only web application should be exposed externally. Database and other services shouldn’t be exposed externally for incoming connections.
Products, Components, Endpoints and Findings
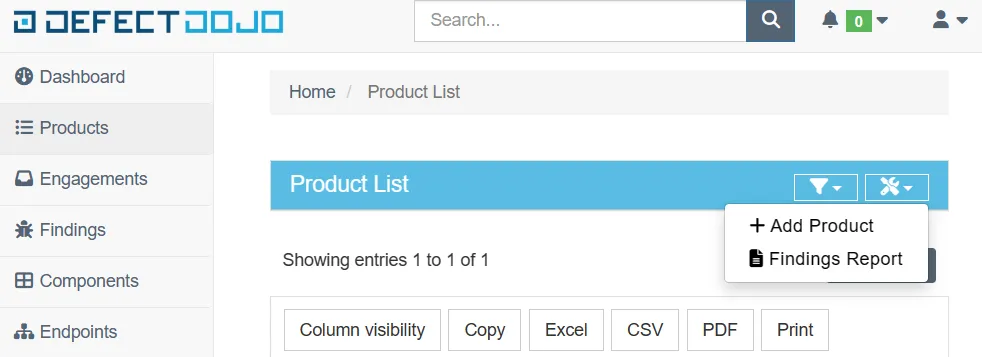
DefectDojo allows users to create products and components. Each product may have a number of components. Security finding can be associated with component and has to be linked to product. Product can be created by clicking on Products from left menu → Tools Icon from top right corner → Add Product. This procedure is presented below:
The product contains a number of data fields such as:
- product name,
- description,
- product manager (a user),
- technical contact (a user),
- team manager (a user),
- product type (which needs to be added before creating a product),
- business criticality,
- platform,
- lifecycle
…and more.
When a product is created, it can be accessed from Products menu. The following screenshot presents how a product page looks like for a newly created product:
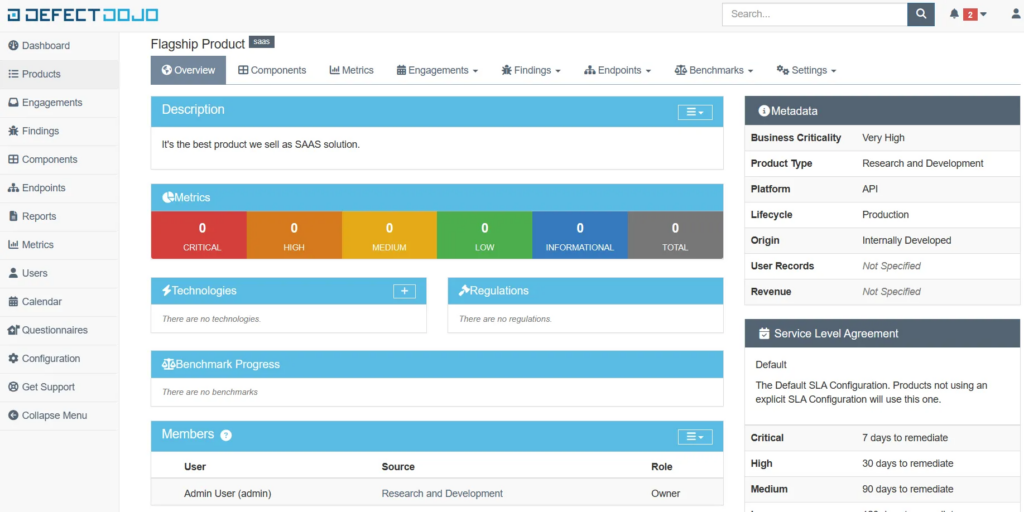
When the product is created, also new vulnerabilities can be added. New vulnerabilities can be created from a product page after clicking on Findings → Add New Finding or by creating a new engagement by clicking on Engagements → Add New […] Engagement. I used the first method and the form is presented below:
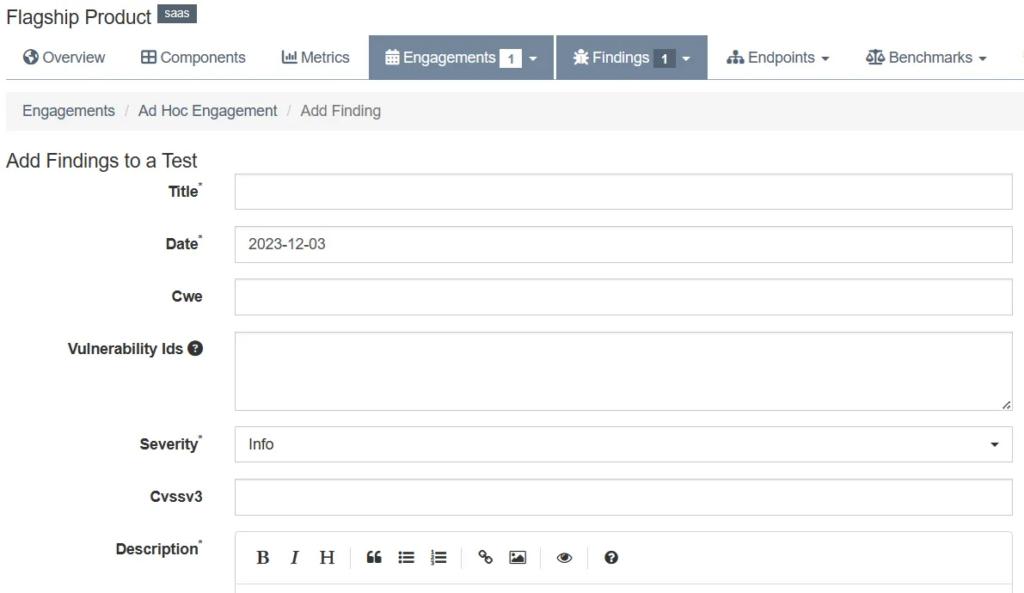
Each finding has a number of fields that can be propagated. Based on my experience, it contains all of the crucial fields that are helpful for vulnerability management. You can add description, steps to reproduce, CVSS vector and score, severity, component name and its version and much more data. Maybe the only field that I found missing is Exploit Prediction Scoring System (EPSS). About EPSS you can read in my previous article:
I created a finding named “Server Side Request Forgery” and it can be observed below on a list of open findings.
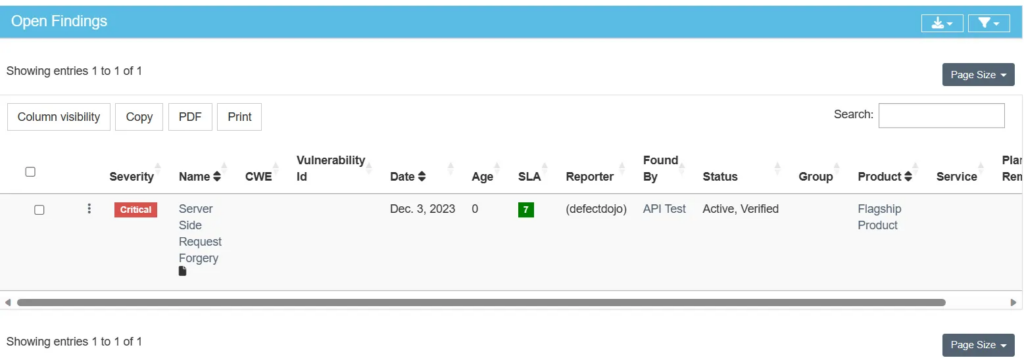
As you can observe, on the above list “Server Side Request Forgery” finding is affecting “Flagship Product”. From this list each finding can be closed as a False Positive, Duplicate, Out of Scope or can go through a risk acceptance process. From my experience, this list would be a most visited place when managing vulnerabilities.
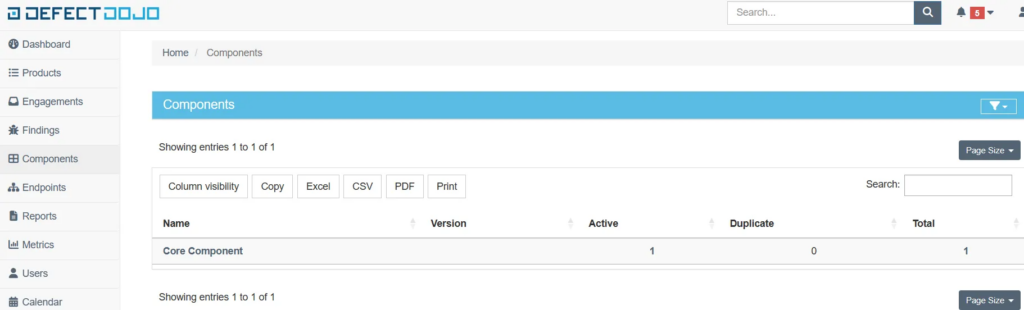
Furthermore, when you add a component name while creating a finding, the component will be automatically created and added to Components section. In this way, I created a “Core Component” of “Flagship Product” created earlier.
Last but not least, DefectDojo allows to manage a list of endpoints and hosts. They can be added after clicking on Endpoints from the left menu. After creating an endpoint, it’s possible to attach a finding to this endpoint in the finding edit form.
Security Engagements and Credentials
DefectDojo provides a cool feature of tracking security engagements. It is useful for tracking any internal or external activities related with security testing. Each engagement is associated with a list of tests that might be performed as a part of the assessment. As a result of these tests there might be security findings identified.
As I mentioned in the previous section, security findings can be created through a product page, so firstly there has to be a product created. Engagement can be created in a similar way. Firstly, you need to open a chosen product page and an engagement can be created by clicking on Engagements → Add New […] Engagement button. The form for creating that, is presented below:
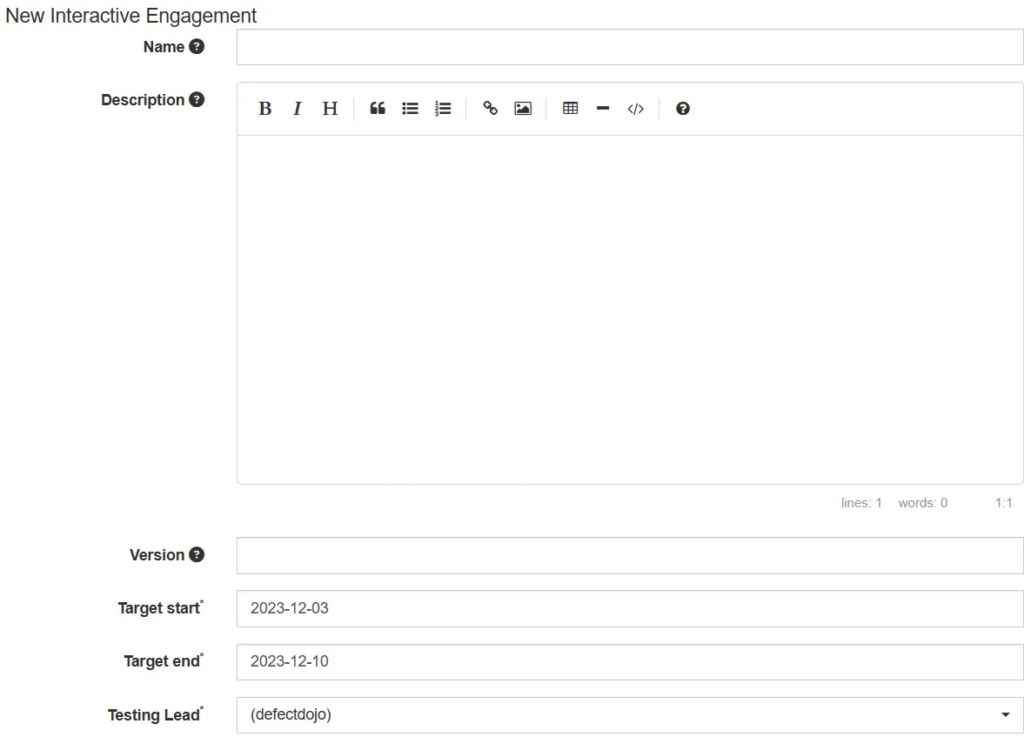
After providing all of the data, there can be a test created and new findings added in a similar way to the presented in the previous section.
Furthermore, for on-going engagements Credential Manager can be utilised. Credential Manager can specify which credentials should be available for a chosen product. As a result, such credentials can be used during an engagement by penetration testers with access to DefectDojo. It might be a pretty effective way of sharing credentials with penetration testers across a number of engagements.
User Management
DefectDojo allows to manage users and groups of users. Each user can be added to the chosen group. Each user may have a role assigned on the product level. So, a user could have one role for a chosen product and a different role for another product. For example, there might be user “Jesse” who will be a Maintainer of only chosen product without access to other products. Also, the role can be assigned through groups on a global level. For example, there might be a user “Walter” being in a group with assigned Maintainer role. As a result, he could be a Maintainer of all of the products.
In practice, such user management seems good enough to restrict access based on products and provide administrative access through user groups.
Integrations
The platform provides a number of integrations. At the time of writing this article DefectDojo had over 150+ integrations. Those integrations may allow for integrating with security scanners, CI/CD solutions, task management platforms such as JIRA and many more.
Furthermore, the platform has API which can be accessed by privileged users. API can be used to import new findings from external sources by users with a dedicated role — API_Importer. More details about the API can be found in the official documentation — DefectDojo API v2 | Documentation.
Summary
In my opinion, DefectDojo is a great tool for Vulnerability Management program for organisations with at least hundreds of vulnerabilities ingested from various sources. This tool provides a number of features for tracking security assessments and vulnerabilities as their output. Furthermore, it contains security questionnaires for each component / product which allows to assess their sensitiveness in context of security.
DefectDojo is a really roboust open-source tool, however, for smaller organisations, there are more effective ways to build Vulnerability Management process in a short amount of time. Those ways may provide less features than offered by DefectDojo but in smaller organisations those features are not must-have and you still would be able to effectively track vulnerabilities lifecycle. DefectDojo is a really good platform when you need a full-fledged process with a number of integrations. Also, the price of its open-source version is very convincing as it’s equal to 0$ 🙂
To summarise my review, here is a list of pros and cons:
Pros:
- open-source solution with a large community (over 3k stars and 378 contributors on GitHub)
- vulnerability lifecycle / workflow ready to use out of the box
- tracking components / products with dedicated security questionnaires
- 150+ integrations with popular platforms such as security scanning tools
- bi-directional integration with JIRA
- basic dashboards with metrics ready to use out of the box
- ASVS benchmarks
- finding templates
- automated deduplication capabilities
Cons:
- design from User eXperience is not user-friendly at the beginning
- self-hosted deployment might be challenging from maintenance perspective
- for smaller organisations it might be too complex





