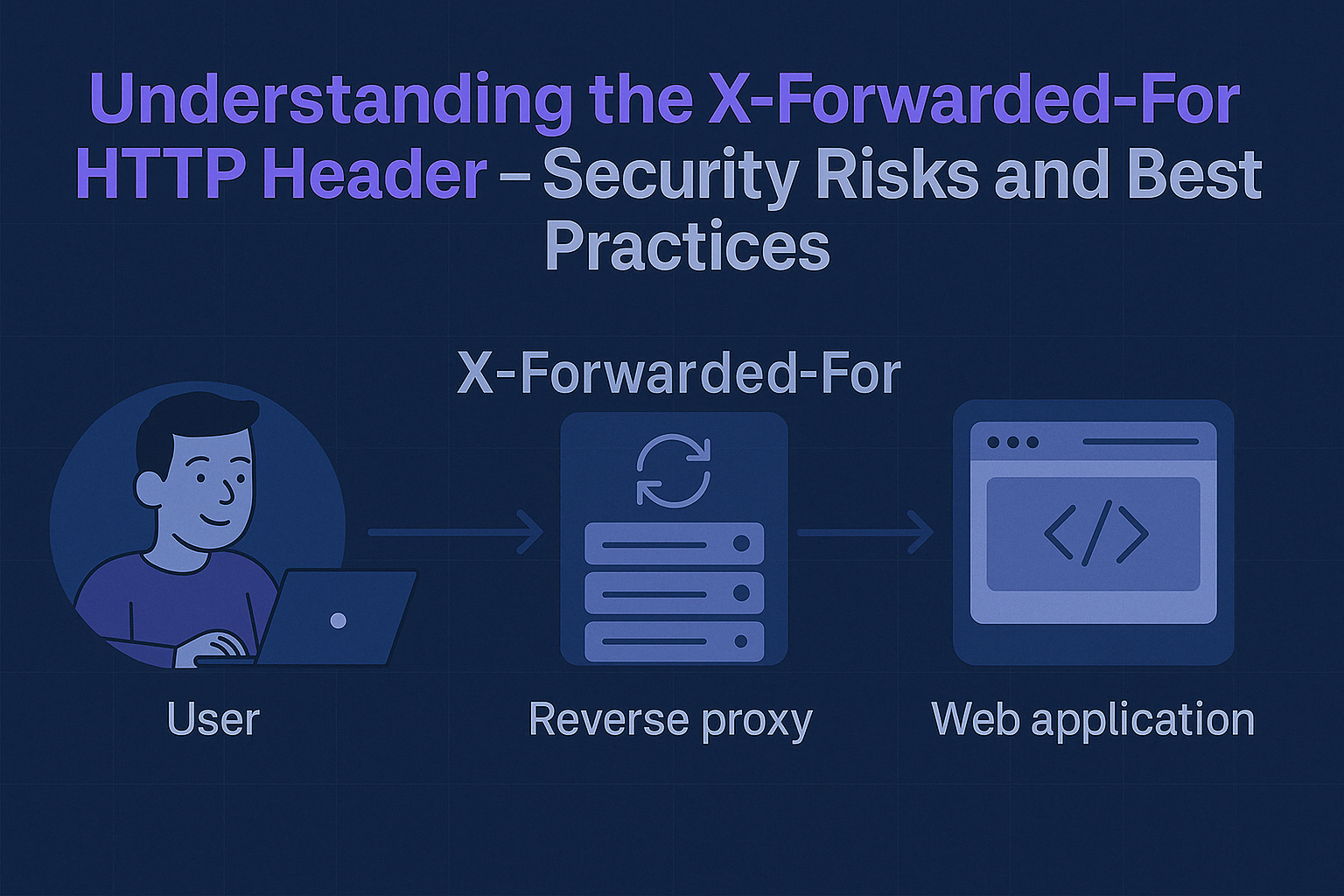
Presenting how to use X-Forwarded-For HTTP header in a practical way. Describing security risks and best practices.
Building AI Agents to Solve Security Challenges

Introduction Artificial Intelligence (AI) has become one of the hottest topics in IT, especially since the public release of ChatGPT. For many, AI is the future of modern technology, which will speed up work and solve various challenges automatically. For others, particularly skeptics, AI (especially LLM-based AI) is viewed as…
Broken Function Level Authorization — Web API Security Champion Part V

Explaining one of the most common web API vulnerability classes — Broken Function Level Authorization in a practical manner. Providing a case study example based on the Damn Vulnerable RESTaurant API, including methods for identifying and preventing these vulnerabilities.
Unrestricted Resource Consumption in a Password Reset — Web API Security Champion Part IV

Presenting an Unrestricted Resource Consumption vulnerability class using a password reset feature as an example.
Web API Security Champion Part III: Broken Object Property Level Authorization (OWASP TOP 10)

Broken Object Property Level presented in a practical way with methods for identifying and preventing vulnerabilities based on OWASP.
Web API Security Champion Part II: Broken Authentication (OWASP TOP 10)

Explaining one of the most common web API vulnerability classes - Broken Authentication in a practical manner. Providing a case study example based on the Damn Vulnerable RESTaurant API, including methods for identifying and preventing these vulnerabilities.
Comparing DefectDojo Pro and OWASP Edition for DevSecOps
A review of DefectDojo Pro — a paid version of a well-known vulnerability management solution: Does DefectDojo Pro address all the pain points of DefectDojo OWASP Edition?
Vulnerability Management with DefectDojo — is it great for DevSecOps?

Presenting capabilities of DefectDojo in context of Vulnerability Management for DevSecOps and traditional application security engineers.
Prioritising Vulnerabilities Remedial Actions at Scale with EPSS

In this article, I’m presenting the Exploit Prediction Scoring System and its practical use cases in tandem with Common Vulnerability Scoring System.
Web API Security Champion: Broken Object Level Authorization (OWASP TOP 10)

Explaining one of the most common web API vulnerability classes - Broken Object Level Authorization in a practical manner. Providing a case study example based on the Damn Vulnerable RESTaurant API, including methods for identifying and preventing these vulnerabilities.