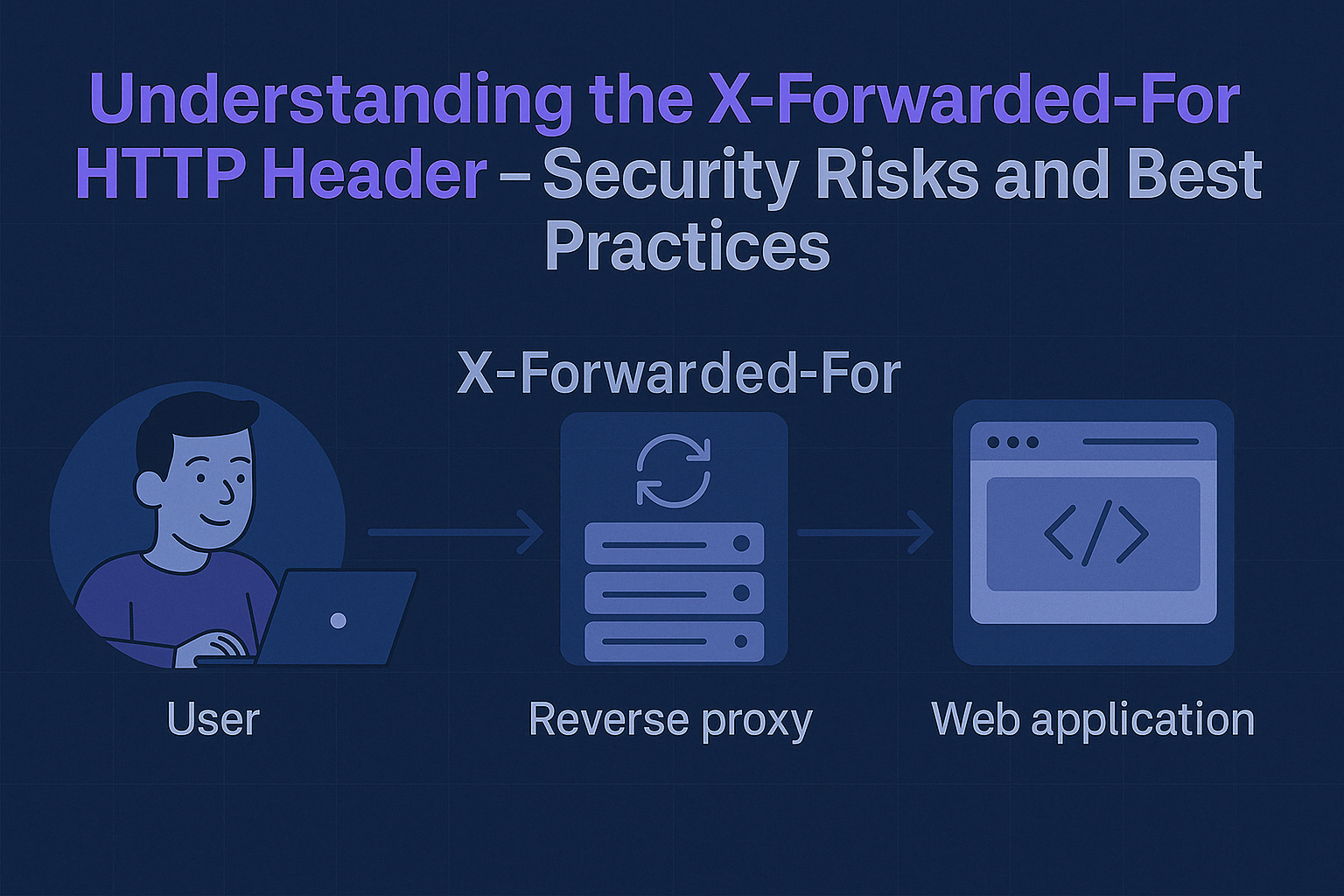
Presenting how to use X-Forwarded-For HTTP header in a practical way. Describing security risks and best practices.
DevSec Selection #28 – Auth Bypass in Next.js, IngressNightmare K8s RCE, TRAIL Threat Modeling

Intro Hi everyone! I hope you had a great weekend. This edition starts with IngressNightmare — a series of vulnerabilities that may lead to unauthenticated remote code execution in Kubernetes. The linked article thoroughly presents the exploitation process and requirements to perform an effective attack. If you work with Next.js,…
DevSec Selection #27 – Wiz Acquired, tj-actions/changed-files GitHub Action Compromised, Useful Open-Source Tools

Intro Hi everyone! Over the past few days, the application security world has been anything but boring. Google acquired Wiz for $32 billion. In the announcement released by Google, we read that Google will continue working with Wiz, which will still be available to customers through a number of partners…
DevSec Selection #26 – Identifying Security Bugs with AI, Semgrep Rules for Detecting Malicious Code and WhoAMI

Intro Hi everyone! I hope you’re doing great. This edition is a little later than usual because I went down a rabbit hole last week, working on a personal project using the recently released Claude 3.7 Sonnet LLM and GitHub Copilot in agentic mode. I’m a developer who started programming…
DevSec Selection #25 – Top 10 Web Hacking Techniques of 2024, Secure by Design in Google, All PortSwigger Solutions

Intro Hi everyone! I hope you have a great weekend. In this edition, I have another portion of materials that you won’t want to miss! If you enjoy cutting edge research articles, you will enjoy 8 Million Requests Later: We Made The SolarWinds Supply Chain Attack Look Amateur. This research…
DevSec Selection #24 – DeepSeek Database Leak, OSV-Scanner v2, Opengrep

Intro Hey, The beginning of this year has been pretty interesting from a product security perspective. In recent weeks, we have observed a number of great articles, tools, and events. DeepSeek V3 was released as an open-source AI model that brought a significant attention and it didn’t take long to…
DevSec Selection #23 – Security AI Agent, Malicious NPM Packages Targeting Cursor, 2024 CVE Review

Intro Hi everyone! I hope you had a wonderful holiday season and a fantastic start to 2025! After the Christmas break, I’m back with several interesting security articles and news updates to share. To summarize 2024, I highly recommend checking out the 2024 CVE Data Review article. It provides essential…
Building AI Agents to Solve Security Challenges

Introduction Artificial Intelligence (AI) has become one of the hottest topics in IT, especially since the public release of ChatGPT. For many, AI is the future of modern technology, which will speed up work and solve various challenges automatically. For others, particularly skeptics, AI (especially LLM-based AI) is viewed as…
DevSec Selection #22 – Google Password Heist, Supply-Chain Firewall, Vanir and Kubernetes Goat

Intro Hey everyone! This year, I’ve shared 22 newsletter editions with you, and I hope you found valuable articles and materials in them. As this is the last edition of the year, I want to wish you a happy and calm Christmas, spent doing your favorite activities. Relax, load your…
DevSec Selection #21 – WordPress Critical Authentication Bypass, Comparison of Enterprise SAST/DAST and Google Dorks for Bug Bounty

Intro Hi everyone! I hope you’re doing great. Recently, we observed a number of high-severity vulnerabilities affecting various popular products.In this newsletter edition, you will find a couple of great technical vulnerability writeups presenting identified security issues with code examples. For anyone interested, I recommend an article about an authentication…