This article presents mechanisms and ideas for detecting malicious applications installed on Android devices that abuse the AccessibilityService feature. It focuses on identifying these applications from the perspective of legitimate apps.
A Practical Approach to SBOM in CI/CD Part III — Tracking SBOMs with Dependency-Track
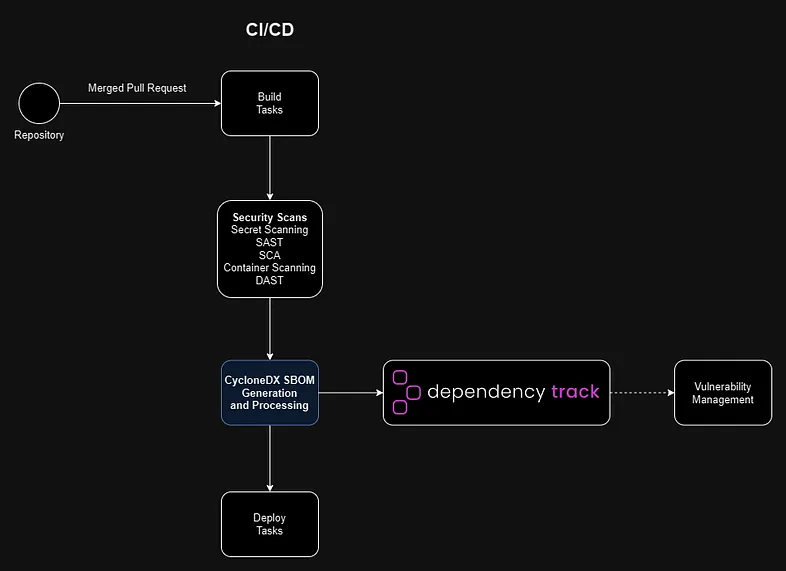
This article covers automated SBOM projects tracking with Dependency-Track. It presents how SBOM can be uploaded to Dependency-Track via API.
A Practical Approach to SBOM in CI/CD Part II — Deploying Dependency-Track
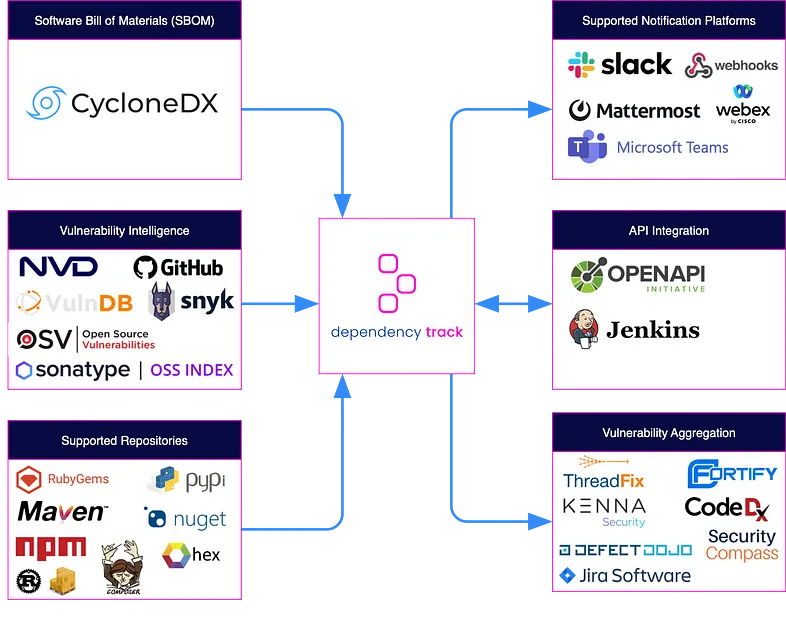
The guide presents how to deploy Dependency-Track with Docker Compose and Helm Charts in Kubernetes. It provides a review of Dependency-Track.
A Practical Approach to SBOM in CI/CD Part I — CycloneDX
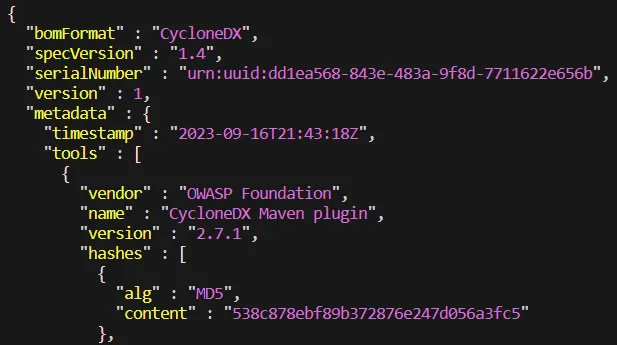
In this article, I’m presenting practical use cases for implementing SBOM generation and its benefits. The article covers the concept of SBOM, its advantages, popular formats and practical implementations for both Java and Python projects.
Introduction to Security in SDLC with SAST for Developers and Security Engineers
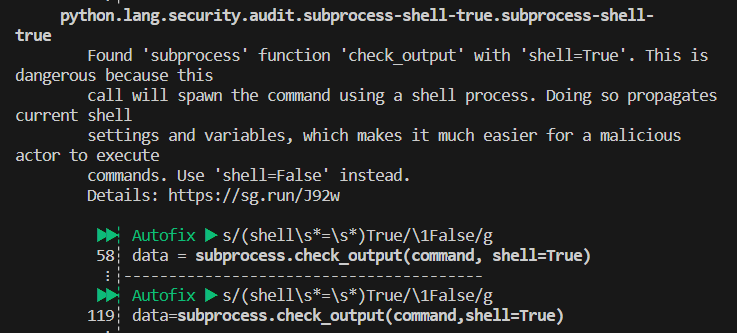
Presenting an introduction Static Application Security Testing with examples how SAST and secrets detection can be implemented in SDLC. This article covers what is SAST and its advantages. Furthermore, it describes how SAST can be included in various SDLC stages with real world examples.






